When you setup single-server Sitecore Commerce 9 instance for staging or demo environment you need to take care of additional settings to make it work with custom domain name. Here I will try to cover all of them for XC instance installed on Azure virtual machine, but it should be similar for your on-premise server.
Hostnames in Configuration Files
- Business Tools app: Set EngineUri, IdentityServerUri and BizFxUri in file SitecoreBizFx\assets\config.json:
|
1 2 3 4 5 6 7 8 9 10 11 |
{ "EnvironmentName": "HabitatAuthoring", "EngineUri": "https://hostname.westeurope.cloudapp.azure.com:5000", "IdentityServerUri": "https://hostname.westeurope.cloudapp.azure.com:5050", "BizFxUri": "https://hostname.westeurope.cloudapp.azure.com:4200", "Language": "en", "Currency": "USD", "ShopName": "CommerceEngineDefaultStorefront", "LanguageCookieName": "selectedLanguage", "EnvironmentCookieName": "selectedEnvironment" } |
- Identity Server app: Set AppSettings\Clients\RedirectUris (you can also add whole new entry) in file SitecoreIdentityServer\wwwroot\appsettings.json:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
... "Clients": [ { "ClientId": "CommerceBusinessTools", "ClientName": "CommerceBusinessTools", "AccessTokenType": 0, "AccessTokenLifetimeInSeconds": 3600, "IdentityTokenLifetimeInSeconds": 3600, "AllowAccessTokensViaBrowser": true, "RequireConsent": false, "RequireClientSecret": false, "AllowedGrantTypes": [ "implicit" ], "RedirectUris": [ "http://hostname.westeurope.cloudapp.azure.com:4200", "http://hostname.westeurope.cloudapp.azure.com:4200/?", "https://hostname.westeurope.cloudapp.azure.com:4200", "https://hostname.westeurope.cloudapp.azure.com:4200/?" ], "PostLogoutRedirectUris": [ "http://hostname.westeurope.cloudapp.azure.com:4200", "http://hostname.westeurope.cloudapp.azure.com:4200/?", "https://hostname.westeurope.cloudapp.azure.com:4200", "https://hostname.westeurope.cloudapp.azure.com:4200/?" ], "AllowedCorsOrigins": [ "http://hostname.westeurope.cloudapp.azure.com:4200/", "http://hostname.westeurope.cloudapp.azure.com:4200", "https://hostname.westeurope.cloudapp.azure.com:4200/", "https://hostname.westeurope.cloudapp.azure.com:4200" ], "AllowedScopes": [ "openid", "dataEventRecords", "dataeventrecordsscope", "securedFiles", "securedfilesscope", "role", "EngineAPI" ] } ... |
- For all commerce engine roles set AppSettings\SitecoreIdentityServerUrl and AllowedOrigins in file {CommerceAuthoring/Ops/Minions/Shops}\wwwroot\config.json:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
... "AppSettings": { "SiteTitle": "Sitecore Commerce Engine", "BootStrapFile": "Global", "DeploymentId": "Deployment01", "EnvironmentName": "HabitatShops", "EncryptionProtectionType": "Machine", "EncryptionCertificateHash": "Enter a valid certificate thumbprint for a PXF file. X-509 not supported yet", "EncryptionSID": "Enter a valid SID for a domain registered user", "EncryptionKeyStorageLocation": "c:\\Encryption-Keys\\", "SitecoreIdentityServerUrl": "https://hostname.westeurope.cloudapp.azure.com:5050", "AllowedOrigins": [ "https://hostname.westeurope.cloudapp.azure.com", "https://hostname.westeurope.cloudapp.azure.com:4200" ], "AntiForgeryEnabled": false, "UseHttpsInKestrel": true, "SslPort": 5000, "SslPfxPath": "wwwroot/localhost.pfx", "SslPfxPassword": "sitecore" } ... |
- For all commerce engine roles set Policies\$values\Host in {CommerceAuthoring/Ops/Minions/Shops}\wwwroot\data\Environments\PlugIn.Content.PolicySet-1.0.0.json:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 |
{ "$type": "Sitecore.Commerce.Core.PolicySet, Sitecore.Commerce.Core", "Id": "Entity-PolicySet-ContentPolicySet", "Version": 1, "IsPersisted": false, "Name": "ContentPolicySet", "Policies": { "$type": "System.Collections.Generic.List`1[[Sitecore.Commerce.Core.Policy, Sitecore.Commerce.Core]], mscorlib", "$values": [ { "$type": "Sitecore.Commerce.Plugin.Management.SitecoreConnectionPolicy, Sitecore.Commerce.Plugin.Management", "Host": "hostname.westeurope.cloudapp.azure.com", "SitecoreDatabase": "master", "UserName": "admin", "Domain": "sitecore", "Password": "b", "ConnectionLeaseTimeout": 60000, "AuthRequestUrl": "sitecore/api/ssc/auth/login", "Protocol": "https" }, { "$type": "Sitecore.Commerce.Plugin.Content.DefaultContentPathsPolicy, Sitecore.Commerce.Plugin.Content", "ContentPaths": { "$type": "System.Collections.Generic.List`1[[System.String, mscorlib]], mscorlib", "$values": [ "/sitecore/Commerce/Commerce Control Panel" ] } } ] } } |
Certificates in Configuration Files
- For all commerce engine roles set thumbprint of your storefront site in Certificates\Certificates\Thumbprint (you can also add whole new entry) in file {CommerceAuthoring/Ops/Minions/Shops}\wwwroot\config.json:
|
1 2 3 4 5 6 7 8 9 |
"Certificates": { "Certificates": [ { "Thumbprint": "76879429EB10AC4B44F5EFEEB8F338D3C484563D", "DefaultRoles": [ "sitecore\\QA", "sitecore\\Commerce Business User" ] } ], "CertificateHeaderName": "X-CommerceEngineCert" } |
To get certificate thumbprints, call PowerShell script Get-ChildItem -path cert:\LocalMachine\My and copy value for the certificate used for your sites.
Commerce Tools in Launchpad
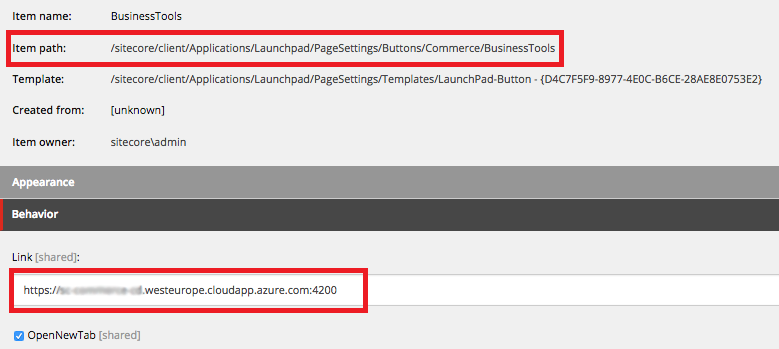
In core database change the Link field value in /sitecore/client/Applications/Launchpad/PageSettings/Buttons/Commerce/BusinessTools item:
Storefront host name
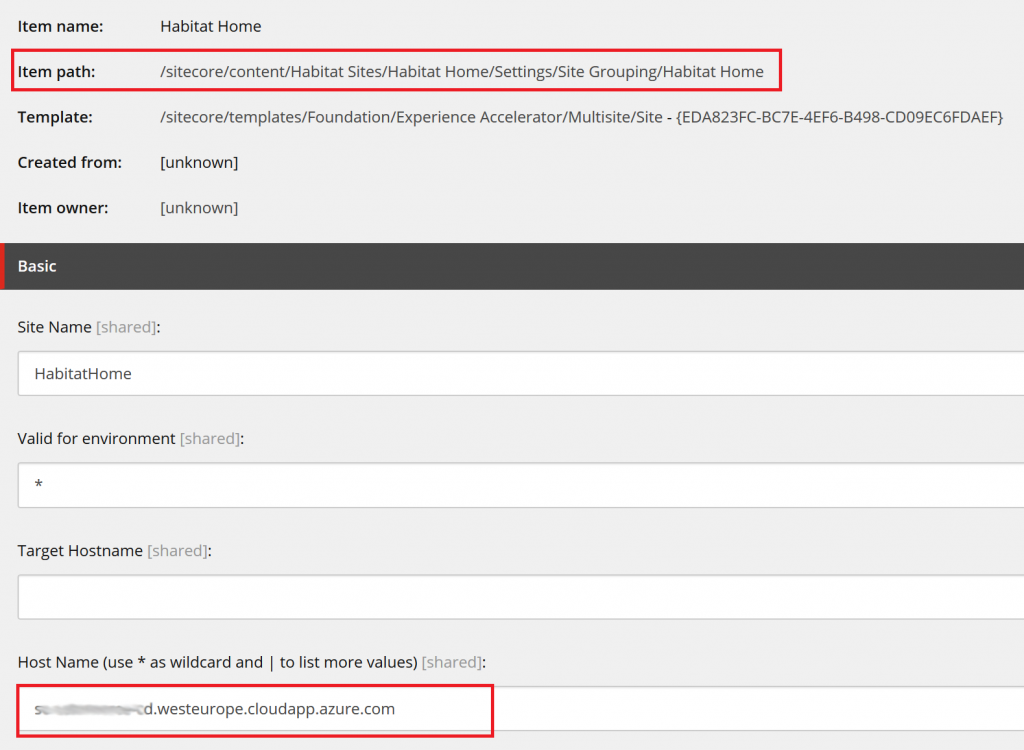
In master database change the Host Name field value in /sitecore/content/{Sites}/{Site}/Settings/Site Grouping/{Site} item:
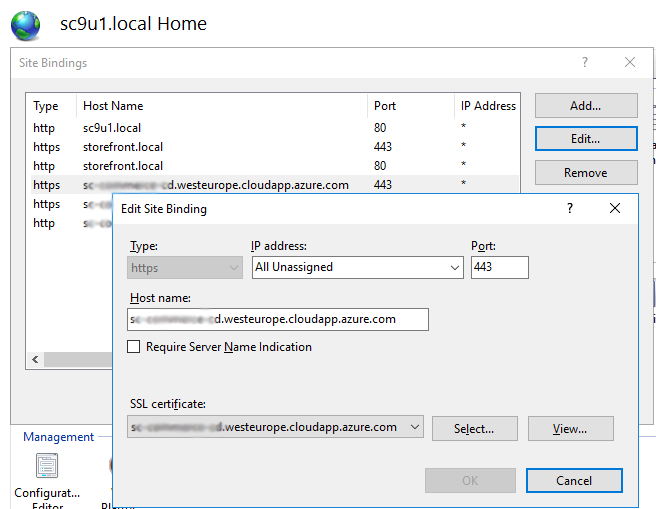
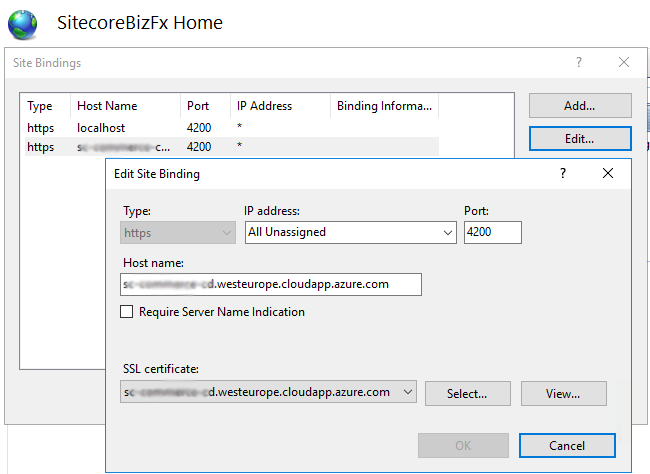
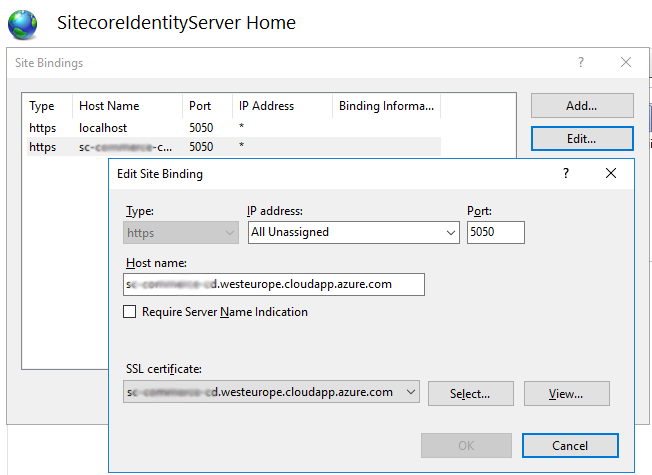
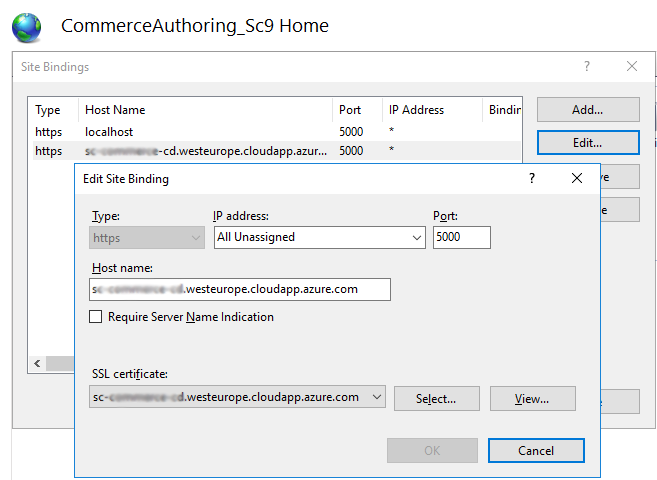
Hostnames in IIS
Configure IIS site bindings, port number and select SSL certificate for:
- Sitecore (storefront) site:
- Commerce business tools (BizFx):
- Identity Server:
- Commerce authoring service:
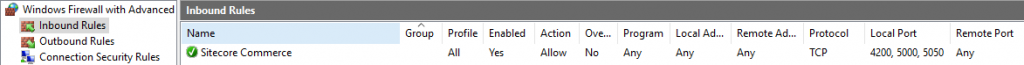
Local Firewall Settings
Add inbound rule for ports 4200, 5000, 5050 in local firewall on VM:
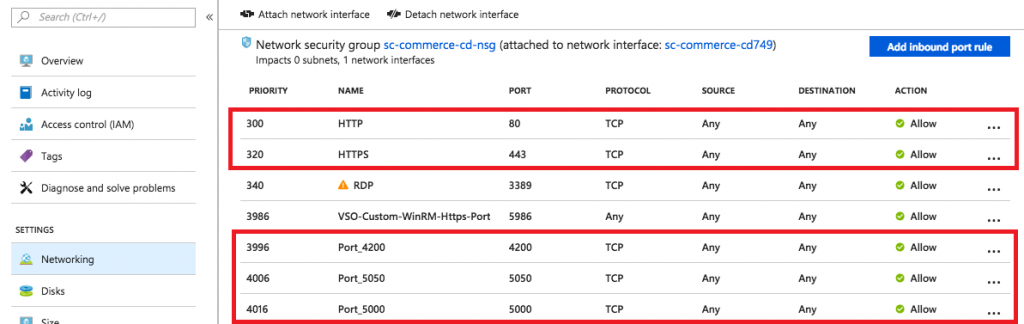
Firewall Settings in Azure Portal
Add inbound rules for ports 4200, 5000, 5050 (and also for 80 and 443 if missing) in VM Networking settings in Azure Portal: