This guide is for development environment only. The goal is to configure external access to Sitecore 9.1 installed on Azure VM as quick as possible. It shouldn’t be used on production due to self-signed certificates usage and reduced security.
Sitecore 9.1 is another step forward into micro services architecture in Sitecore world. In 9.1 Sitecore introduced new web application called Identity Server, responsible for user authentication. Previous version of this app was already used in Sitecore Commerce 9, now it’s integral part of the platform.
Taking this into consideration, there is additional configuration required, for example when we try to allow external access to our development installation of Sitecore 9.1 on Azure VM. Here is the step-by-step guide how to achieve this:
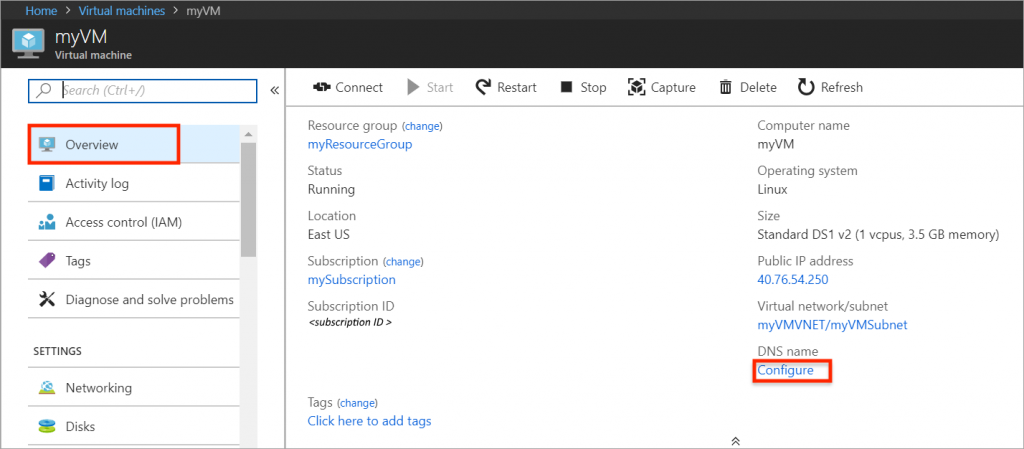
1. Configure DNS name for Azure VM
You can set DNS name for your VM in Overview settings in Azure Portal. By default your free domain name will have suffix depending on Azure region, for example:
http://smartsitecore.westeurope.cloudapp.azure.com
 2. Configure Firewall Settings in Azure Portal
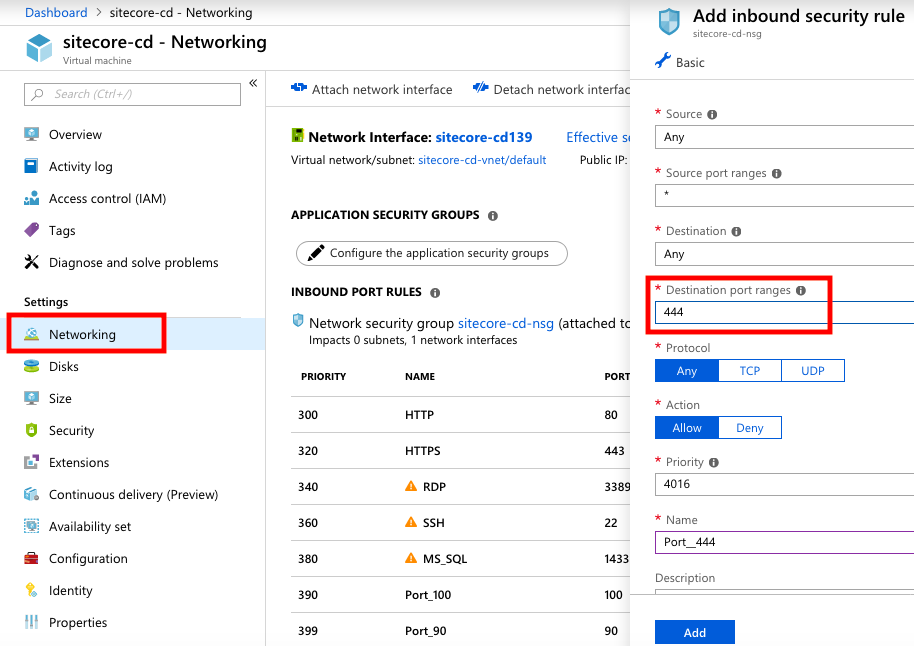
2. Configure Firewall Settings in Azure Portal
In Azure Portal in Networking settings we add new inbound rule for ports used by Sitecore application (by default it will be 80, or 443) and Identity Server (we use custom port number):
 3. Configure Firewall Settings in Azure VM
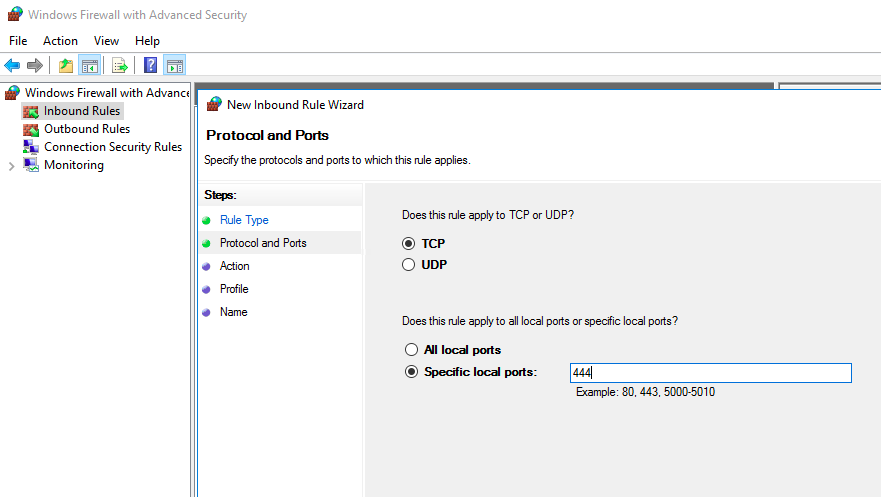
3. Configure Firewall Settings in Azure VM
We need to configure also local firewall on Azure Virtual Machine for all custom ports used:
 4. Configure IIS Bindings in Sitecore and Identity Server
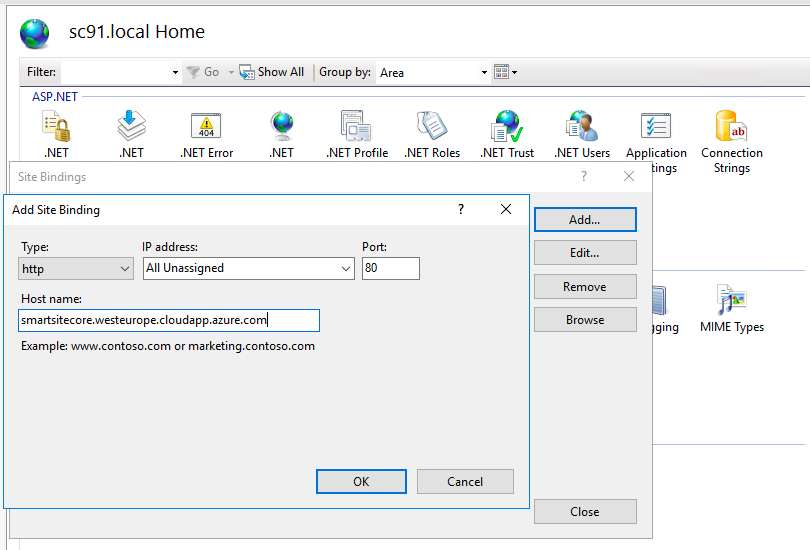
4. Configure IIS Bindings in Sitecore and Identity Server
We can now configure our host name in IIS Bindings on Azure VM for Sitecore:
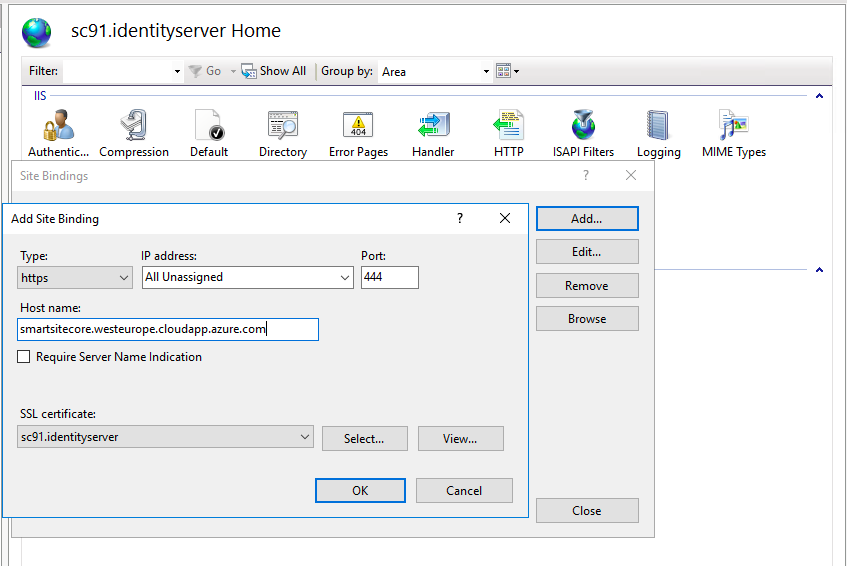
 Next let’s do same for Identity Server. We use https with same certificate as for local domain:
Next let’s do same for Identity Server. We use https with same certificate as for local domain:
 5. Configure Identity Server Host in Sitecore Application
5. Configure Identity Server Host in Sitecore Application
Now we need to point to our new Identity Server host name in Sitecore application. We can do it with Sitecore configuration patch. Create patch file and place it in \App_Config\Include\ folder in Sitecore website directory:
|
1 2 3 4 5 6 |
<?xml version="1.0" encoding="utf-8" ?> <configuration xmlns:patch="http://www.sitecore.net/xmlconfig/" xmlns:role="http://www.sitecore.net/xmlconfig/role/"> <sitecore role:require="Standalone or ContentDelivery or ContentManagement"> <sc.variable name="identityServerAuthority" value="https://smartsitecore.westeurope.cloudapp.azure.com:444/" patch:instead="*[@name=identityServerAuthority]" /> </sitecore> </configuration> |
Original setting is placed in \App_Config\Sitecore\Owin.Authentication.IdentityServer\Sitecore.Owin.Authentication.IdentityServer.config file.
6. Configure Allowed Domain in Identity Server Application
In last step we configure Identity Server to set allowed Sitecore application domains which can connect to Identity Server. We change it in \Config\production\Sitecore.IdentityServer.Host.xml file in Identity Server web folder:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
<?xml version="1.0" encoding="utf-8" ?> <Settings> <Sitecore> <IdentityServer> ... <AccountOptions> <PasswordRecoveryUrl>http://smartsitecore.westeurope.cloudapp.azure.com/sitecore/login?rc=1</PasswordRecoveryUrl> </AccountOptions> <Clients> <DefaultClient> <AllowedCorsOrigins> <AllowedCorsOriginsGroup1>http://smartsitecore.westeurope.cloudapp.azure.com</AllowedCorsOriginsGroup1> </AllowedCorsOrigins> </DefaultClient> ... </Clients> </IdentityServer> </Sitecore> </Settings> |
If your Sitecore application uses custom port number you just write it there without tailing slash (/). For example: http://smartsitecore.westeurope.cloudapp.azure.com:91
Finally we should be able to open our page http://smartsitecore.westeurope.cloudapp.azure.com and login to Sitecore using http://smartsitecore.westeurope.cloudapp.azure.com/sitecore. This one will redirect us to Identity server url: https://smartsitecore.westeurope.cloudapp.azure.com:444/account/login where we’ll need to accept self-signed certificate to continue.
